The University of Pennsylvania offers threat protection and antivirus software solutions for faculty, staff, and students. For computers managed by Wharton Computing (typically faculty, staff, and the public computers in labs, classrooms, and hallways), the Crowdstrike software must be installed and running. For unmanaged computers (typically student computers, and those not managed by Wharton Computing), the University provides Sophos Home free of charge.
For more information such as recommendations and helpful tips, please see our full Virus Protection article.
Before You Start
Managed v. Unmanaged: Wharton Computing manages many computers on campus -- these are called "managed computers". Wharton Computing also supports people who are using computers that aren't managed by Wharton Computing -- these are called "unmanaged computers".
- Managed computers: purchased by Wharton/Penn; built, configured, and maintained by Wharton Computing staff.
- Unmanaged computers: purchased by individuals or by Wharton/Penn using personal funds.
Are You Already Protected?
The first step is to determine whether you are already protected. Recommendations at Wharton differ depending on whether you are faculty, staff, or student and whether Wharton Computing is managing your computer.
Unmanaged Computers (Students, Faculty & Staff with Unmanaged or Personal Computers)
Student computers and some personal computers owned by faculty and staff are "unmanaged" -- they are not part of the Wharton Computing-managed computing environment. These computers should have antivirus protection installed -- we recommend Sophos Home (for Macs) or Windows Defender (for Windows 10).
Step 1: Determine if you are already protected
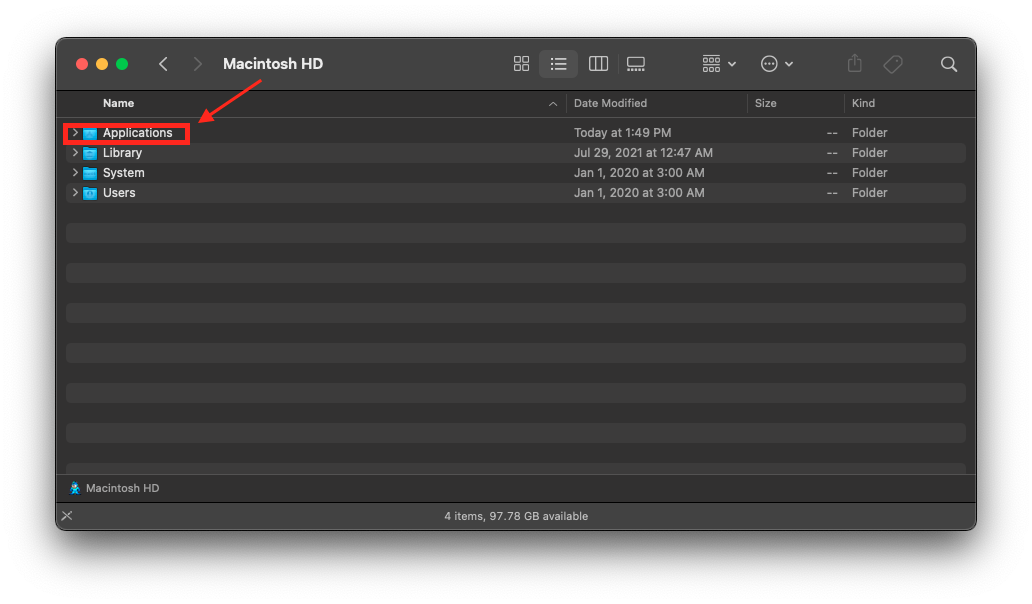
- Mac: If you are using the Univerisity-provided Sophos antivirus, you should see the Sophos Home icon in the menu bar. Or, you can navigate to your applications folder and confirm whether you have installed antivirus software. (Sophos Home is recommended by Wharton and Penn. )
- Windows 10: Navigate to Settings -> Update & Security -> Windows Security -> Virus & threat protection. Confirm that Windows Defender is turned on.
Step 2: Download and Install the Correct Software
Use the Antivirus Software chart below to determine which software to install.
Managed Computers (Staff, Faculty)
Wharton Computing uses the Crowdstrike software to protect staff and faculty machines that are managed by Wharton Computing. (Student computers are not managed by Wharton Computing.)
Mac
If you have a Mac that is managed by Wharton Computing, contact your IT Support Team to confirm whether it is protected.
Windows 10
- Navigate to Settings -> Update & Security -> Windows Security -> Virus & threat protection.
- You should see this image for CrowdStrike:
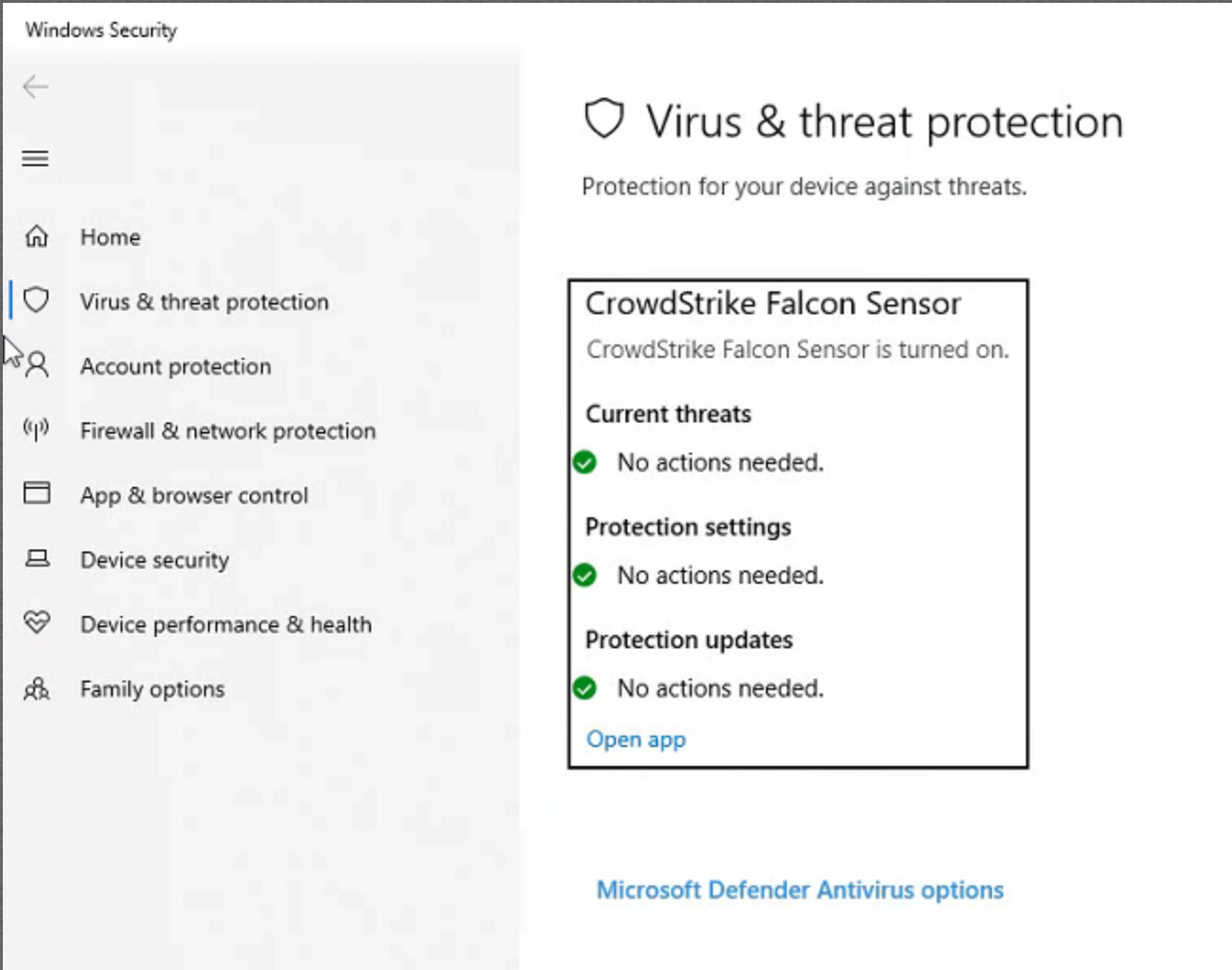
- If you do not see it, contact your IT Support team immediately.
Choosing Your Antivirus Software
There are several conditions that will determine which steps you take to install the appropriate antivirus software: who you are, and what kind of computers you are using.
|
|
Student | Faculty | Staff |
| Unmanaged Mac | Sophos Home | Sophos Home | Sophos Home |
| Managed Mac | N/A | Crowdstrike | Crowdstrike |
| Unmanaged Windows | Windows Defender | Sophos Home | Sophos Home |
| Managed Windows | N/A | Crowdstrike | Crowdstrike |
Antivirus Download Links
For unmanaged computers, Wharton Computing recommends using Sophos Home software on MacOS devices. Windows 8 & 10 devices are already protected by the built-in antivirus software, Windows Defender.
|
MacOS
|
Windows 10
|
Windows 10 (if Defender is not an option)
|
Sophos Home FAQs
Here are a few questions we hear from users about Sophos Home:
If you are satisfied with your current antivirus software and are able to update the virus definition files regularly, you can continue the use of your current antivirus software, but you may need an additional anti-spyware program. If you are not able to update the virus definition files, or if your antivirus subscription is expired and you don't plan to renew it, you will need to switch to Sophos Home. The University pays for a Sophos Home subscription that includes virus definition updates, spyware scans, virus scans, and a host of other protections. It is also supported by Wharton Computing, so you can get assistance with the program should you encounter any problems. Yes, Wharton Computing offers support for Sophos Home and will be able to help you install and configure the antivirus software.What if I already have antivirus software?
Why should I switch to Sophos Home?
Will I get technical support if I switch to Sophos Home?
Questions?
Students - email support@wharton.upenn.edu.
Faculty - contact your Academic Distributed Representative (login required).
Staff - email admin-support@wharton.upenn.edu.
For more information regarding security threats and antivirus software, you can also contact the Wharton Information Security Office at security@wharton.upenn.edu.
This article provides information on protecting yourself from viruses, malware, and other malicious software. It lists recommended protection software, helpful tips, and what to do next if you think you've been infected.
Faculty and Staff: Computers purchased by the University will automatically have Crowdstrike (a centrally-managed antivirus program) installed on them. These computers will not need the software listed below.
For personal computers, Penn offers the site-licensed Sophos Home, free of charge, to members of the Penn community using the links below.
If you have questions or concerns please reach out to Wharton Computing using the links in Questions, below.
Antivirus Software
Most Antivirus software now requires a subscription. If you prefer not to maintain a subscription, we recommend using Sophos (free to members of the Penn Community) or Windows Defender (for Windows machines).
Faculty and Staff who are using a computer managed by Wharton Computing already have antivirus installed automatically and can skip this section.
Active Defenders
- Windows → Sophos Homeis offered by the University for free. Best for Staff and Faculty use.
- Windows 10/11 → Windows Defender is the default antivirus software on Windows 10 & above. Best for Student use.
- MacOS → Sophos Homeis also offered for MacOS by the University.
Scanners
- MalwareBytes scans your computer for any potential malicious or suspicious software & processes.
Helpful Tips
Be Aware of Sites & Attachments
As computers become more networked and standardized, it gets easier and easier to catch computer viruses. You can get viruses from downloads over the internet, from opening e-mail attachments, or from another infected system or device.
Many self-propagating viruses will mail themselves to you before the original sender has discovered that his/her machine is infected. Be suspicious of any attachments, but be extra vigilant about inappropriate subject lines and attachment titles (for example, if someone you barely know sends you an e-mail called ILOVEYOU).
Back Up Data Frequently
Some viruses are so damaging that they will render your files useless or unrecoverable. In that case, your only hope of recovery is with back-ups made prior to infection.
Update, update, update!
Microsoft & software developers frequently release patches to fix known issues for their services. These fixes include known security issues that may leave your computer or program vulnerable to viruses and other attacks. To manually update, press the Windows key + S (  + s), type check for updates, and then click the Check for Updates setting.
+ s), type check for updates, and then click the Check for Updates setting.
Sophos Home
The University of Pennsylvania offers free antivirus software to faculty and staff in the form of Sophos Home. Below are the links to download this software, along with some Frequently Asked Questions.
Faculty and Staff who are using a computer managed by Wharton Computing already have antivirus installed automatically and can skip this section. However, Sophos is available for personal use as well, so can be installed on non-managed machines.
Download Links
Wharton Computing recommends using this software on MacOS devices. Windows 10 & 11 devices are already protected by the built-in antivirus software, Windows Defender.
Note: If you're still running Windows 8/8.1, Wharton Computing recommends updating to Windows 10 for optimal performance if supported by your device.
Windows 8.1, 10, or 11 | Windows 8.1, 10, or 11 | MacOS |
Staff and Faculty | Students | Students |
Sophos Home FAQs
What if I already have antivirus software?
If you are satisfied with your current antivirus software and are able to update the virus definition files on a regular basis then you can continue the use of your current antivirus software, but you might need an additional anti-spyware program. If you are not able to update the virus definition files or your antivirus subscription is expired, you will need to switch to Sophos Home.
Why should I switch to Sophos Home?
The university pays for a Sophos Home subscription that includes virus definition updates and spyware scans in addition to virus scans. It is also supported by Wharton Computing, so you can get assistance with the program should you encounter any problems.
Will I get technical support if I switch to Sophos Home?
Yes, Wharton Computing offers support for Sophos Home and will be able to help you install and configure the antivirus software.
If your computer has a virus...
Students: If you think you have a virus, please stay calm and follow the directions in our Virus Removal article. We also encourage you to call, email, or drop by our Support Office (SHDH 114) in person so we can help with the situation.
Faculty & Staff: Please contact your Wharton Computing Representative or the Wharton Information Security Office at security@wharton.upenn.edu.
Questions?
Students: visit the Student Computing Website.
Faculty: contact your Academic Distributed Representative (login required).
Staff: email admin-support@wharton.upenn.edu.
For more information regarding security threats and antivirus software, you can also contact the Wharton Information Security Office at security@wharton.upenn.edu.
This article will give you an overview of what a firewall is, how it works, and will provide instructions on how to ensure your personal computer's firewall(s) are enabled.
Faculty & Staff: Faculty and Staff using Wharton-imaged or Wharton-provided devices may not be able to change Firewall (Crowdstrike) settings. This article applies only to personally managed computers.
For additional questions or requests, please reach out to your IT support representative or the Wharton Information Security Office at security@wharton.upenn.edu.
What is a firewall?
- A firewall is a network security system that establishes a barrier between a trusted, secure internal network and another network that may not be secure.
- Additionally, a firewall can help prevent hackers or malicious software from gaining access to your computer through a network or the Internet. A firewall can also help stop your computer from sending malicious software to other computers.
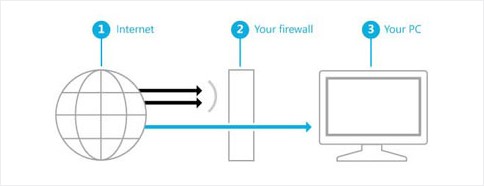
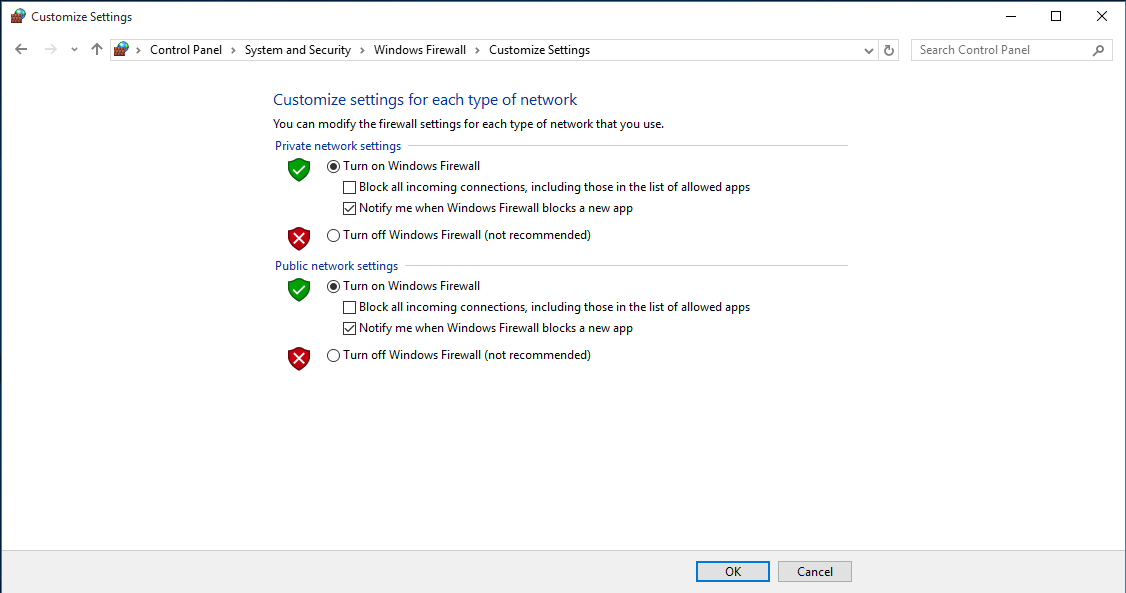
Enable/Disable Firewall
Warning: Only turn off your Firewall if you are installing a separate antivirus software that includes a firewall and active defender.
Windows
Follow Microsoft's directions on how to turn your Firewall on or off.
MacOS
Follow Apple's directions on how to turn your Firewall on or off.
Allow Trusted Applications
You can allow applications you trust. Only choose this option for applications you know are safe.
Questions?
Students - Wharton Computing Student Support
Faculty - Academic Distributed Representatives
Staff - Administrative Support
For more information regarding security threats and antivirus software, you can also contact the Wharton Information Security Office at security@wharton.upenn.edu.
This article covers the update process for Web Browsers.
Faculty and Staff on Wharton-Managed Machines:
Your browsers should update automatically but it's still a good idea to follow the steps listed below.
Web Browsers
Healthy Computing requires regularly updating your computer, but we often forget to update our web browser(s). Since so much of computing now takes place in a web browser, it is considered one of the largest attack vectors for malware.
Most major browsers (e.g. Chrome, Edge, Safari, Firefox, and DuckDuckGo) are quick to fix vulnerabilities and auto-update, and all you need to do is restart your browser regularly! The Wharton Information Security Office recommends restarting your browser each day to allow any applicable updates to apply.
Your open tabs should reappear or if not, you can restore the previous session from the “History” menu in your browser to pick up from where you left off while being up-to-date!
Updating your Browser
There are several ways to update your browsers.
Restart (Updates Automatically)
A restart of your browser usually updates it immediately -- all you need to do is close all open instances of the browser, and restart. Your open tabs should reappear or, if not, you can restore the previous session from the “History” menu in your browser to pick up from where you left off.
Manual Update
You can also manually check your browsers for updates, although how you do it varies by Operating System:
macOS: click the application title in the top menu bar just to the right of the Apple logo, and select “About [Browser Name]” from the menu that appears
For Safari, macOS delivers updates via software updates in Settings; see Update to the latest version of Safari - Apple Support
Windows: click “Help” in the top menu bar of the application, and select either “About [Browser Name]” or “Check for Updates” from the menu that appears.
Browser Resources and Recommendations
For more information on security options for major browsers, here are places to start:
- Chrome: https://support.google.com/chrome/answer/10468685?hl=en&sjid=8263394724745160652-NA
- Microsoft Edge: https://support.microsoft.com/en-us/microsoft-edge/enhance-your-security-on-the-web-with-microsoft-edge-b8199f13-b21b-4a08-a806-daed31a1929d
- Safari: https://support.apple.com/guide/safari/welcome/mac (choose Table of Contents and then Security for your version)
- Firefox: https://support.mozilla.org/en-US/products/firefox/protect-your-privacy
These practices and recommendations also apply to other web browsers that may not be listed here.
Questions?
Contact your Wharton Computing Representative or the Wharton Information Security Office for more information.
The Google Security & Privacy checkups provide a quick and effective way to ensure that your Google account is secure and private. These checklists can be used on any Google account, whether it is personal or school-provided.
Access requirements: Must have an active Google account. Google Security CheckupGoogle's Security Checkup is a great way to ensure that your account is secure and isn't being accessed by anyone but you. It can also help highlight security flaws on your account that may be easily missed.
Google Privacy CheckupGoogle's Privacy Checkup allows you to personalize which types of data Google collects as well as allowing you to manage the visibility of your account.
Questions?Faculty & PhD Students: Academic Distributed Representatives Staff: Administrative Support Students: Wharton Computing Student Support For more information regarding Google Security and Privacy, you can also contact the Wharton Information Security Office at security@wharton.upenn.edu. | ||||
Frequently Asked Questions
Q: I no longer use an app (i.e. G Suite Sync for Outlook) and want to remove its access to my Google Account. How can I do this?
A: The first step of the Google Security Checkup allows you to review and manage any apps that have been granted access to your account.
Q: Are security & privacy checks available for my devices as well?
A: If you are a student, yes! Simply drop by the Tech Center at SHDH-114 and ask to participate in a Device Tune-up & Security Session. If you are faculty or staff, please contact your Academic Distributed Representative or Administrative support, respectively.
Q: What if I notice a device or location that isn't mine has accessed my account?
A: Reset your Google account password as soon as possible, as well as any other passwords that may be the same or similar. Contact your IT support team if you have additional questions (see Questions? above).
This article provides guidance regarding Google's Login Challenges. More specifically, it is designed to describe when they appear, why they appear, and what you can do about it.
Note: This article only applies to students whose Google accounts were created before December 2023.
Account security is of utmost concern for both Google and Wharton Computing. When Google determines that a user is logging in from either:
- An unknown device (new phone, tablet, laptop, or desktop)
- An unusual or new location (different state or country)
They may prompt the user with a login challenge. The login challenge you receive depends on the information you have associated with your account.
Faculty, Staff, and PhD Students
Contact your IT Support Representative or the Wharton Information Security Office at security@wharton.upenn.edu for the best option to use for recovery.
Adding Recovery Information
- Navigate to myaccount.google.com.
- Log in with your Google Account.
- Click the Security tab.
- Scroll down to Ways we can verify it's you.
- Choose a recovery option (phone or email) and follow the instructions to verify your information.
Various Login Challenges
Scenario 1: No recovery information
You will be prompted with the following Login Challenge if you do not have a recovery phone number or a recovery email address associated with your account.
- Enter your mobile phone number.
- You will receive a 6-digit numerical code.
- Enter the code and click next.
Scenario 2: Only recovery phone number
You will be prompted with the following Login Challenge if you only have a recovery phone number associated with your account.
- Choose your preferred option:
- Receive a text at your designated recovery phone number.
- Receive a voice message/call at your designated recovery phone number.
- Confirm your recovery phone number.
Scenario 3: Only recovery email address
You will be prompted with the following Login Challenge if you only have a recovery email address associated with your account.
- Confirm your recovery email address.
- Click Next.
Scenario 4: Both recovery phone number & recovery email address
You will be prompted with the following Login Challenge if you have both a recovery phone number and a recovery email address associated with your account.
- Choose your preferred option:
- Receive a text at your designated recovery phone number.
- Receive a voice message/call at your designated recovery phone number.
- Confirm your recovery phone number.
Additional Note: Other Help
The “Other Help” button provided leads to Google’s account recovery process.
Students: Unfortunately this process will not work for a student’s Google@Wharton account. If you are unable to recover your account with the options provided above, please contact Student Support (students).
Questions?
Students - Wharton Computing Student Support
Faculty - Academic Distributed Representatives (login required)
Staff - Administrative Support (login required)
For more information regarding Google login information, you can also contact the Wharton Information Security Office at security@wharton.upenn.edu.
If your personal computer has a virus, use the steps below to try removing it on your own.
Faculty and Staff should NOT attempt to remove viruses on any machine provided to them by Penn.
If you suspect you have a virus, disconnect your computer from the network, power it off, and contact your Wharton Computing Representative or the Information Security and Privacy Team at security@wharton.upenn.edu right away for assistance.
Virus Removal Procedure
We've compiled a set of simplified steps for PC and Mac to make it easy for you to try and fix your own computer. Students can make an appointment (before 2 pm) with Student Support to have their machines scanned and cleaned if more help is needed.
Before You Start:
- Back up your computer's data to an external hard drive or other source not attached to your computer to prevent any loss of important data.
- Make sure you're comfortable downloading and installing software on your computer.
Windows/PC
The procedure below is simplified for your convenience and remedies most situations.
Virus Removal
- Install & run Malwarebytes --make sure you DECLINE the trial offer, and remove all selected.
- Run Windows Defender or install Sophos Home and run a scan.
Post Removal Checklist
- Check to ensure that an Anti Virus program is installed and running (Windows Defender, Sophos, etc...).
- Check that the Firewall is enabled.
- Check to see if there are any available Windows updates, and download them at your earliest convenience. (Depending on how many updates are pending, this may take anywhere from several minutes to several hours.)
- Check to ensure the computer successfully connects to the Internet.
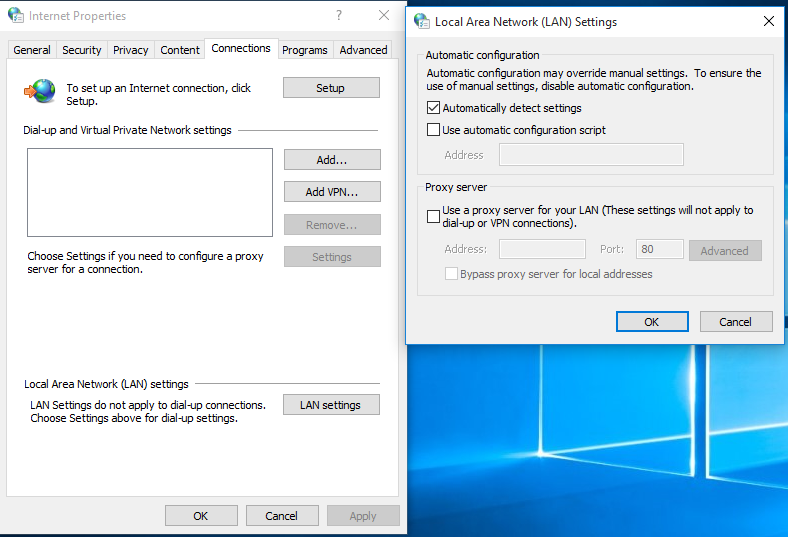
- If the computer does not connect, check to see if the infection enabled a proxy by going to the LAN settings in Internet options.
- If the computer does not connect, check to see if the infection enabled a proxy by going to the LAN settings in Internet options.
Students who are still experiencing complications can make an appointment (before 2 pm) with Student Support to have the computer scanned and cleaned.
Virus Removal Procedure (Mac)
The steps for removing viruses from Macs are fairly straightforward.
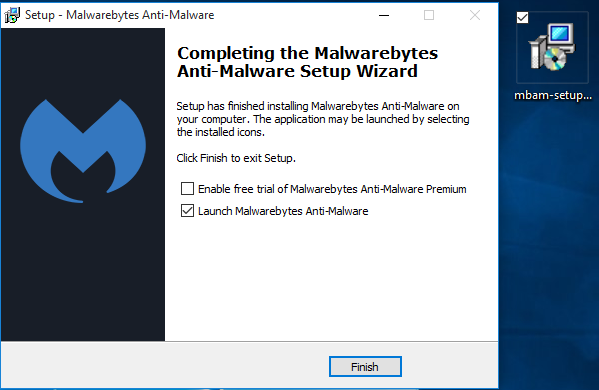
- Download and install Malwarebytes for Mac.
- Open Malwarebytes, and Accept the Terms and Conditions.
- Click Scan, if any items are found, click Delete All.
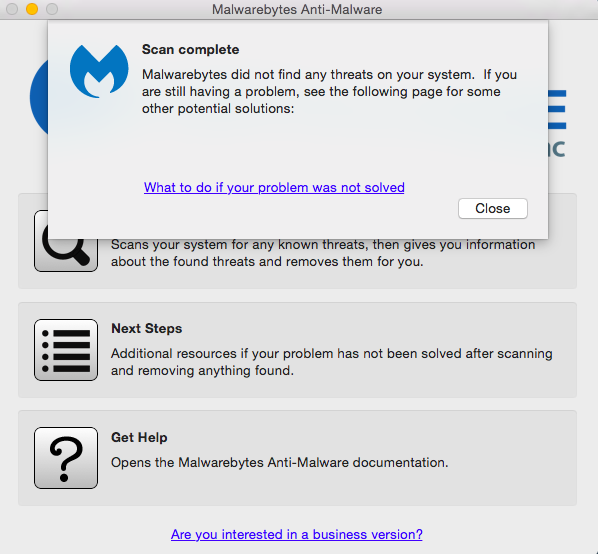
- Restart your computer.
Questions?
Contact your Wharton Computing Representative or the Wharton Information Security Office at security@wharton.upenn.edu for more information.
If you have a LastPass account from the University, please see our directions on migrating your account to Dashlane.
The University provides a premium password management service, Dashlane. Use this article to help you choose and configure the account type that is right for you, and for any Wharton-specific tips. The University also has information on setting up Dashlane.
Dashlane Business Plan
Dashlane business plan accounts are available for University faculty, staff, and employees. They allow you to share credentials with other colleagues securely.
You must use the Dashlane business plan if:
- you use credentials for University resources or work purposes.
- you need to share collections (a shared Dashlane password folder) of credentials with other employees.
To create a Dashlane account tied to Wharton’s business plan, you'll need to receive an invitation emailed to your Wharton email account. To request an invitation to use Dashlane Enterprise, please contact your Wharton Computing representative.
LastPass Enterprise users should automatically receive a Dashlane invitation to their Wharton email account with the subject: “You have been added to UPenn - Wharton on Dashlane.” Follow the instructions in our University Retires LastPass Password Manager article.
If you run into issues with installing the browser plugin see Dashlane's article. We also recommend that you turn on the Account Recovery Methods to ensure you don’t lose all your passwords if you forget your Master Password! See the section on enabling account recovery options, below, for details.
Dashlane Personal Account with Premium Access
Dashlane personal accounts are for everyone in the Penn Community.
Only personal credentials and files should be used with a Dashlane Personal plan.
To obtain a Dashlane Premium account, follow ISC’s Dashlane Premium instructions.
Dashlane is available as an app for your smart phone, and as an extension for your web browser. If you run into issues with installing the browser plugin, you can use this link to install it.
Can I have 2 accounts?
You can have two separate Dashlane accounts, but they must have separate login credentials:
- Dashlane Business: Use this for Wharton and Penn work
- Dashlane Premium: Use this for saving personal credentials.
Additional Information and Best Practices
General
Safari Browser Does Not Work
When using Safari, accepting the invitation from email doesn’t work. You will likely have to use a different browser (eg. Firefox, Chrome).

Note: the Dashlane browser plugin is required to interact with Dashlane. Mac OS has a Dashlane client, but it does not allow access to the full suite of sharing features available in the Mac OS client.
Account Recovery Options
We recommend enabling a password recovery option for your Dashlane account so you have another way to access your password store if you lose your master password. See Dashlane's article on Account recovery key set up .
Store Personal and Business Passwords Separately
ISC and Wharton Security recommend using distinct password manager stores (accounts) to separate your personal passwords:
- Personal passwords: any passwords for personal use, eg. your Netflix account, etc.
- Work passwords: any credentials you use to access work resources.
This is good practice so that a compromise of your personal password manager won’t inadvertently expose University resources and open the University to risk. You can have two separate Dashlane accounts, but they must have separate login credentials. For example:
- Dashlane Business: Use this for Wharton and Penn work
- Dashlane Premium: Use this for saving personal credentials. (Or use a different password manager.)
If you need to store work-related credentials, ask your Wharton Computing representative for an invitation to Wharton’s Dashlane plan.
Dashlane Business Users
Dashlane Business Accounts are Tied to the Wharton Dashlane plan
Using Dashlane Business accounts linked to the Wharton Dashlane Plan means you are part of the school’s Dashlane account and subject to its policies. When a Dashlane Business account is separated from our Wharton Dashlane plan (for example, if you leave the university), your account will lose all data added when it was part of the business account.
Don't Store Personal Passwords in Dashlane Business
We recommend not storing personal passwords in Dashlane Business. If for whatever reason you simply cannot avoid it, please beware of the following:
-
When you leave the University, your Dashlane business account will be removed from the Wharton Dashlane business plan. Any passwords created while part of the Dashlane business plan will be deleted from your Dashlane account.
-
Since it is complicated to export individual passwords, and exporting any work credentials is against policy, we recommend storing all personal passwords in a separate account (either Dashlane Premium or another password manager).
Enable Account Recovery Options
We recommend that you turn on an Account Recovery Method: This will ensure you don’t lose all your passwords if you forget your Master Password! If you forget your Master Password and haven't enabled a recovery method, you may need to reset your account, which erases all your data. Here are the options:
- Option 1: Account Recovery Key
- Option 2: Admin-Assisted Recovery
- Option 3: Biometric Recovery
Business users should enable all 3 options. They need to be set up BEFORE before you need the account recovery service, so make sure to consider this when setting up your account. If you weren’t prompted to do this when you set up your account (or just didn’t do it), see Dashlane's article on setting this up.
Using Dashlane Collections
A Dashlane collection is a shared Dashlane password folder. It works a little differently than in LastPass.
-
In LastPass, credentials were stored inside the shared folder. Everyone with access to the shared folder could see it.
-
In Dashlane, each credential first must be created in the user’s Dashlane storage, and then shared to a Collection. Once each user gains access to the collection, those items then are visible in those users' Dashlane storage as well.
-
When sharing collections, if you share the collection without granting anyone else full (“Manager”) access, then no one else will be able to share it if your Dashlane account gets revoked from the Wharton Dashlane shared account. You should take care to always make sure at least one other person other than yourself has Manager access to a shared collection, otherwise you may end up with a shared collection with passwords and credentials inside it that no one can manage, edit, or delete.
The best way to deal with disruptive behavior in a Zoom meeting is to prevent it from happening in the first place. This article details several ways to secure your Zoom meetings and how you can quickly deal with disruptions in an active Zoom meeting.
You will need:
- An activated Penn Zoom Account before completing any of the tasks in this article.
- Have the host or co-host role in the Zoom meeting.
Best Practices
Zoombombing, wherein participants join Zoom meetings to cause a disruption, can derail any meeting. There are some things that you can do to thwart potential Zoombombers before they even have the chance to enter your meeting.
Don't post meeting information publicly
Only share the Zoom meeting details with attendees. Avoid posting them on a publically accessible website (Canvas sites are only accessible to those people explicitly granted access).
You should also consider not using your Personal Meeting ID. This is a permanent meeting that has set login information. While your PMI is great for sharing with students and co-workers because the login information remains the same, it is less secure since that login information could be shared with others without your knowledge. We recommend setting up individual Zoom meetings for regular work/classes.
Enable Waiting Room
In a Zoom meeting with Waiting Room enabled, the meeting host/co-host has to admit people into the meeting. This allows you to control exactly who can join your meeting.
To enable the Waiting Room for a Zoom meeting as it is taking place (and the host/co-host of):
- Click the Host Tools icon at the bottom of your Zoom meeting window.
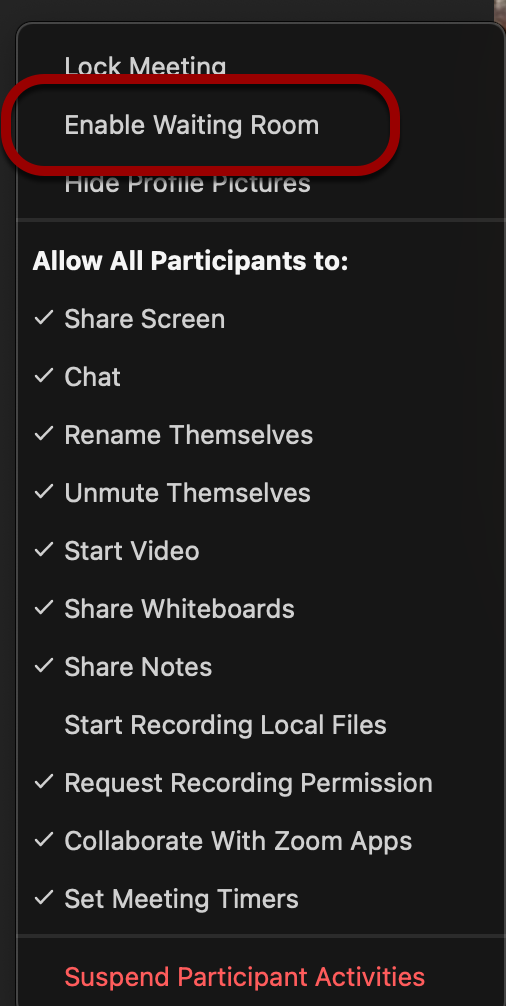
- Click Enable Waiting Room on the Security menu.
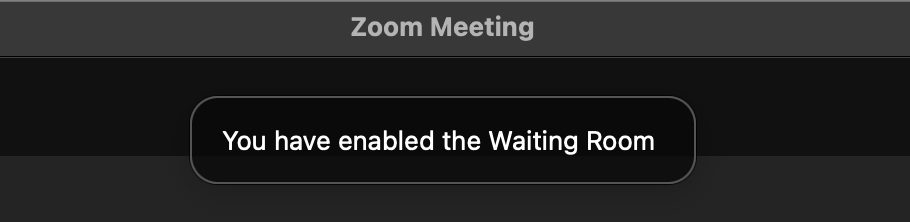
- You'll see an alert that lets you know the waiting room has been enabled for the meeting.
You'll get an alert whenever someone enters the Waiting Room. You can read more about Waiting Rooms in Zoom's documentation.
To enable the Waiting Room for a meeting scheduled in the future:
- Log into https://upenn.zoom.us with your PennKey username and password.
- Click on Meetings in the left sidebar.
- You will see a list of your upcoming meetings. Hover over the meeting you want to change and click the blue Edit button.
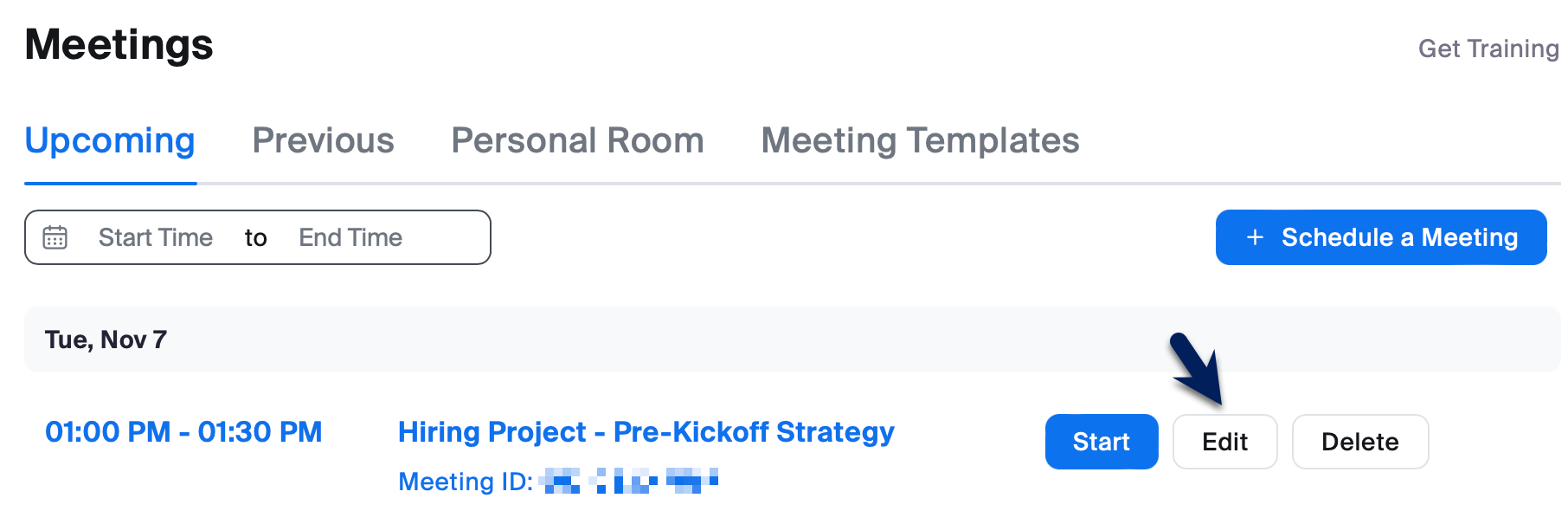
- Scroll down to the Security section and check the box next to Waiting Room.
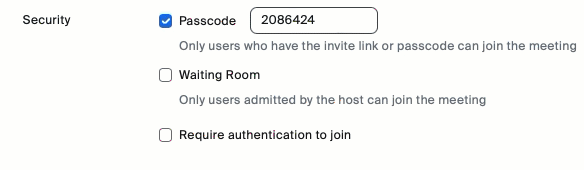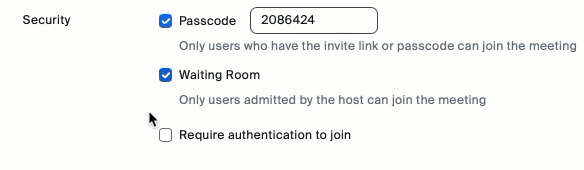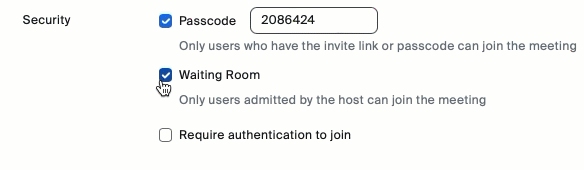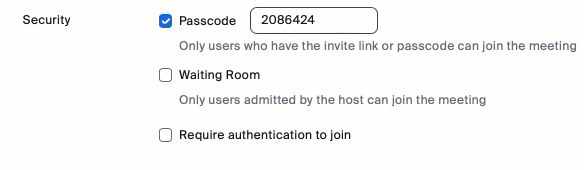
- Click Save, and your meeting is updated.
To have all of your new Zoom meetings have Waiting Room enabled by default:
- Log into https://upenn.zoom.us with your PennKey username and password.
- Click on Settings on the left sidebar.
- This should open the Meeting settings, with Waiting Room near the top.
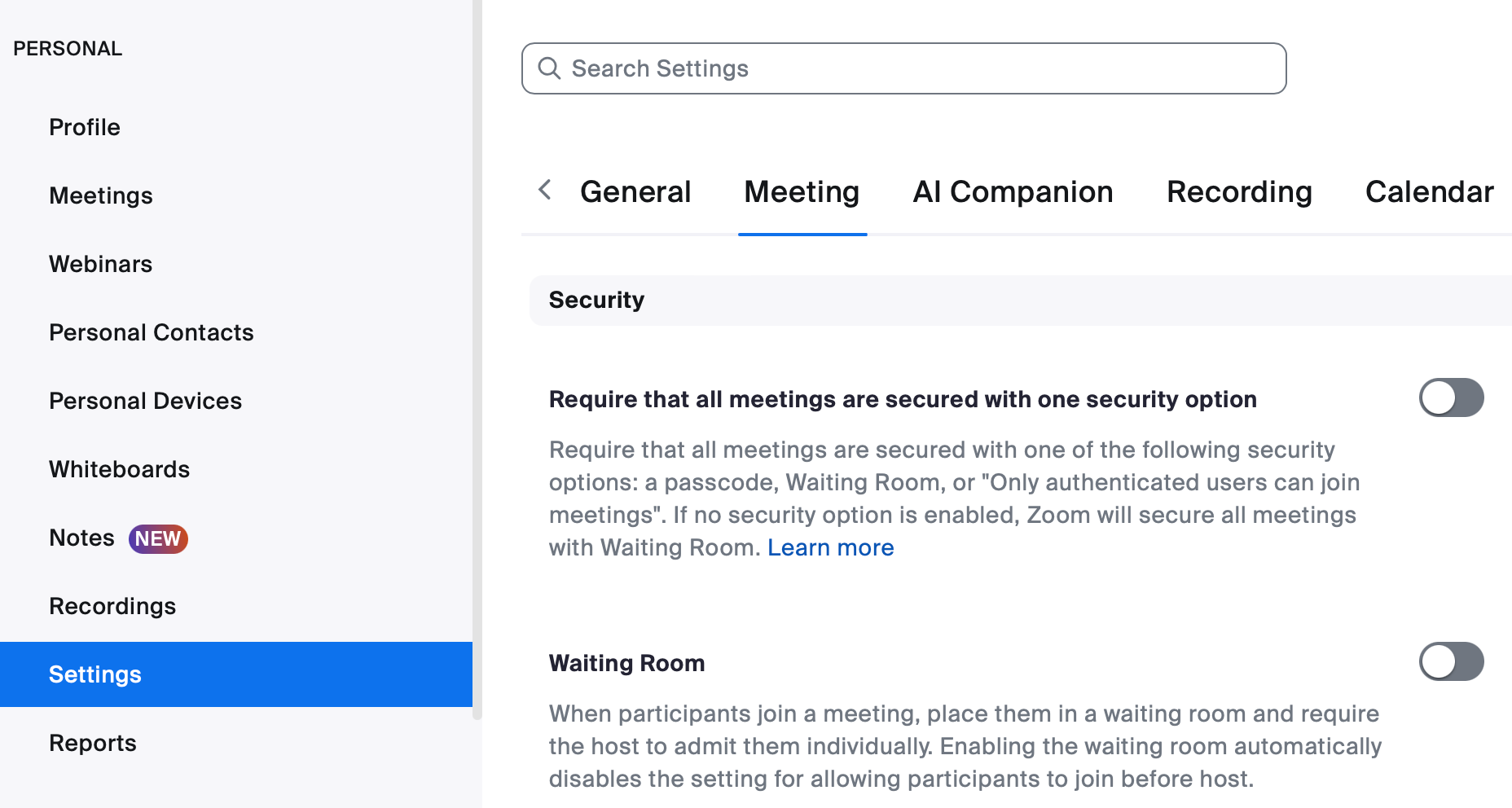
- Toggle Waiting Room on.
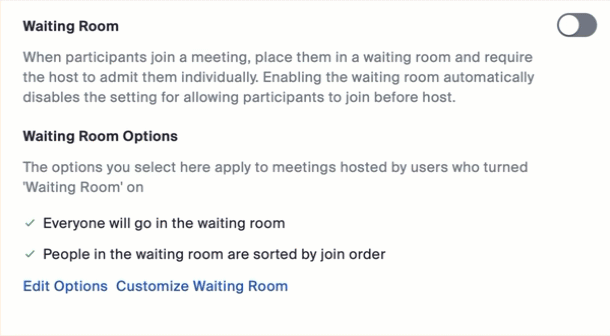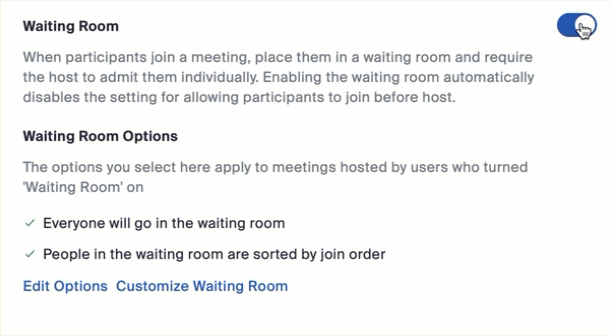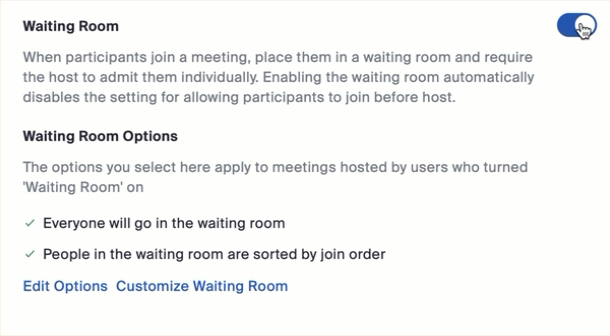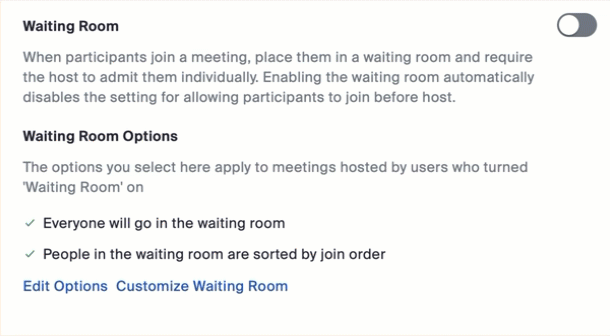
- Click Edit Options if you'd like to change who should go into the waiting room ("users not in your account" means non-Penn users), among other things.
- Changes are saved automatically, so any meetings you create going forward will have a Waiting Room.
If you enable "Allow Authenticated Users Only" (see the next section for more information on this setting), you can allow authenticated users to skip the Waiting Room and be automatically allowed into the meeting by following these directions after logging into https://upenn.zoom.us with your PennKey username and password:
- Click Settings.
- Click Security.
- Under the Waiting Room section, click Edit Options.
- Change "Who should go into the waiting room" to "Users not in your account." This will allow Penn users to skip the Waiting Room whilst, non-Penn users, or unauthenticated Penn users, will need to be allowed into the meeting from the Waiting Room.
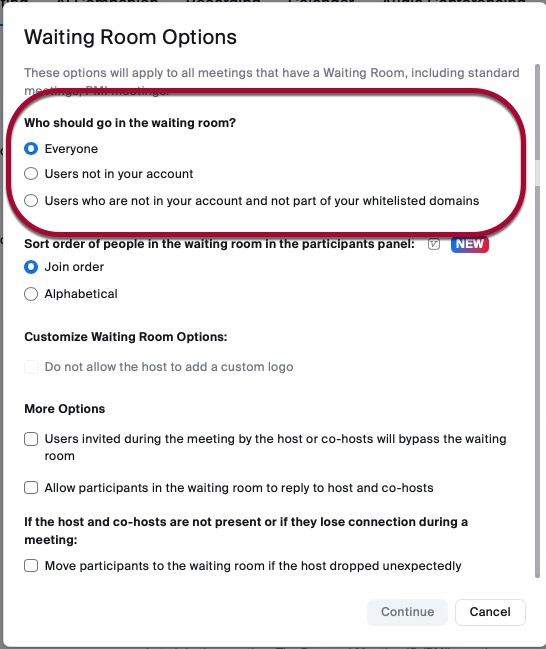
- Click Continue.
Authenticated users only
You can require that all attendees be logged in with their Penn accounts or a Zoom account before they can join your meeting. You can limit it to (the following list goes from least to most inclusive and is additive):
- Penn users only
- Anyone with a Zoom account
- Specific exceptions can be added per meeting (i.e., santa@northpole.com can join without having to authenticate, but everyone else has to since they might be naughty).
You can require authentication on a per-meeting basis or by default for all meetings:
On an individual meeting
New Meeting
- Launch Zoom.
- Schedule a new meeting.
- Scroll through the Schedule Meeting window and check the box next to "Only authenticated users can join."
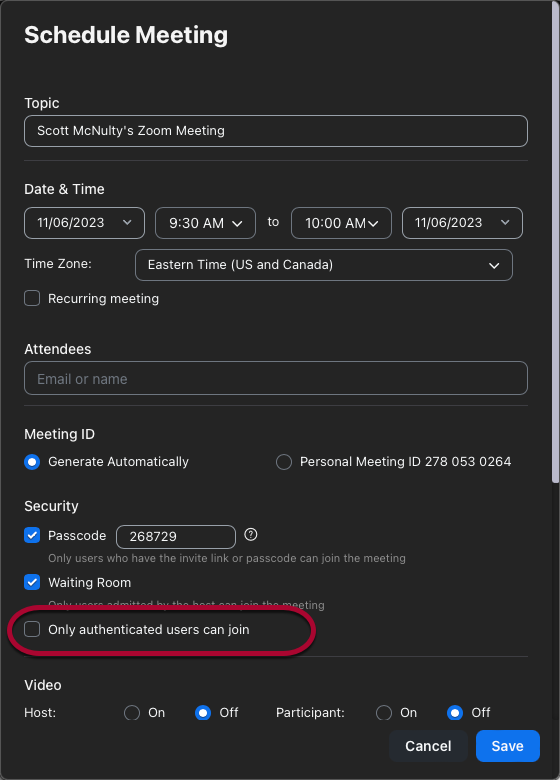
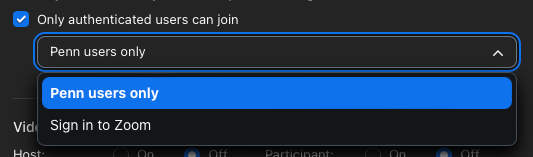
- Select either Penn users only (the default) or Anyone with a Zoom account from the dropdown.
- Continue scheduling your meeting as usual.
Existing Meeting
The best way to force authentication on an existing meeting is to edit the settings via https://upenn.zoom.us:
- Log into https://upenn.zoom.us with your PennKey username and password.
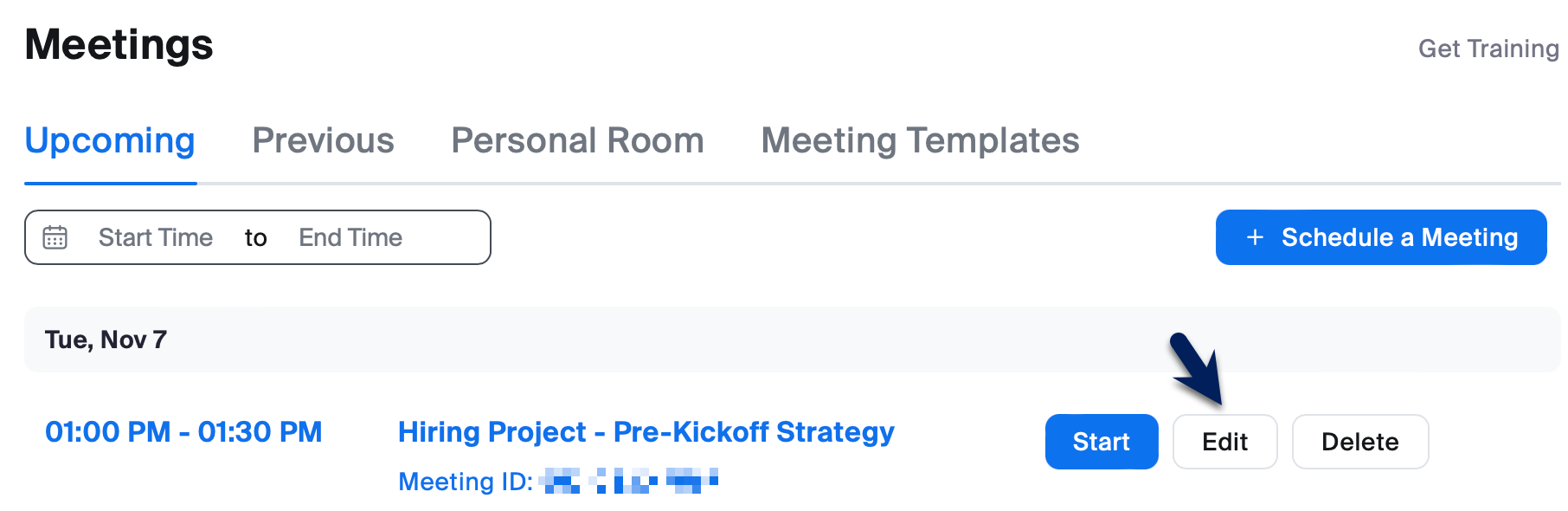
- Hover over the meeting you'd like to edit from your Upcoming Meetings.
- Click the Edit button that appears as you're hovering over the meeting.
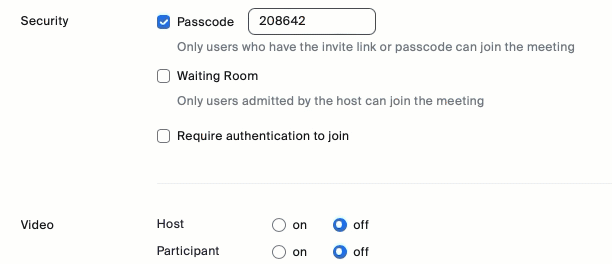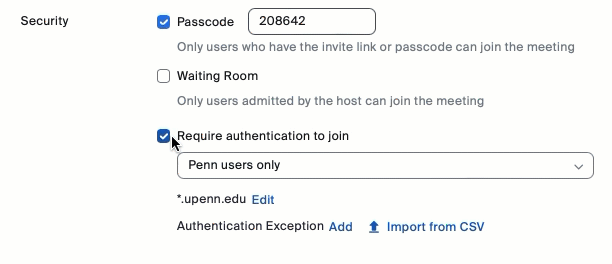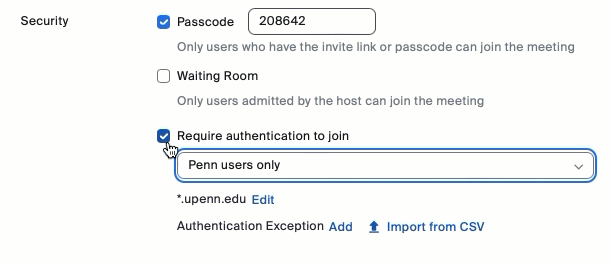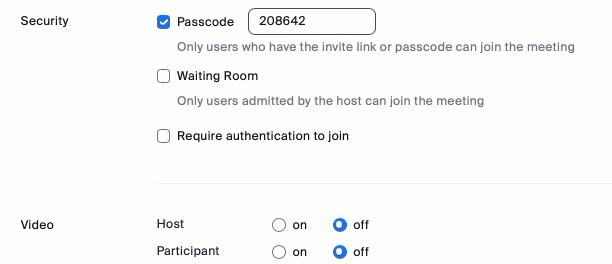
- Check "Require authentication to join" in the Security section.
- Select either Penn users only (the default) or Anyone with a Zoom account from the dropdown.
- Click Save.
Allowing Exceptions
Authentication Exceptions allow you to list people who don't have to authenticate to enter a meeting that requires it. This allows you to limit your attendees to Penn folks (or people with a Zoom account) but include non-Penn guest speakers. Here's how:
- Log into https://upenn.zoom.us with your PennKey username and password.
- Hover over the meeting you'd like to edit from your Upcoming Meetings.
- Click the Edit button that appears as you're hovering over the meeting.
- Click Add next to "Authentication Exception" under "Require authentication to join" in the Security section.
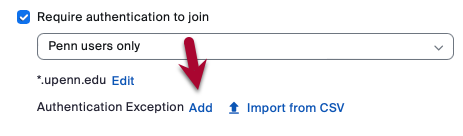
- Type the exception's full name and email address.
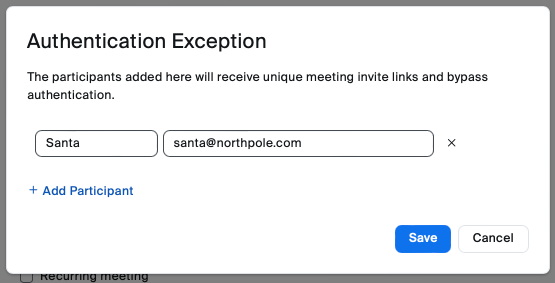
- Click Add Participant to add more exceptions.
- Click Save to save the exceptions.
- Click Save to save the settings for the meeting.
Making this a Default Setting
You can require authentication for all your Zoom meetings going forward by logging into https://upenn.zoom.us with your PennKey username and password and following these directions:
- Click Settings.
- Click Security.
- Scroll down until you see "Only authenticated meeting participants and webinar attendees can join meetings and webinars."
- Click the toggle next to that section to turn it on (the toggle displays blue when a feature is active).
- Your settings are automatically saved, and now, each Zoom meeting you schedule will require attendees to authenticate.
During Your Meeting
Despite following all of our best practices, disruptions could occur in a Zoom meeting in which you're the host (or co-host). There are a few Zoom tools that make it easy to deal with a disruptive participant quickly:
- Remove Participant - Disruptive participants are easy to remove once identified.
- Lock Meeting - Locking your meeting stops any further participants from joining.
- Suspend All Participant Activities - The most severe option of the bunch; this will stop all activity in the meeting so you can gather your thoughts and identify the disruptive participants who should be removed.
The following three sections detail each of these features in turn.
Remove Participant
If you can identify the disruptive participants, you can remove them from your Zoom meeting:
- Click on the Participants icon at the bottom of the Zoom window to show the Participants list if it isn't already showing.
- Find the person you'd like to remove and hover over their name in the list.
- Click on More to reveal a list of options.
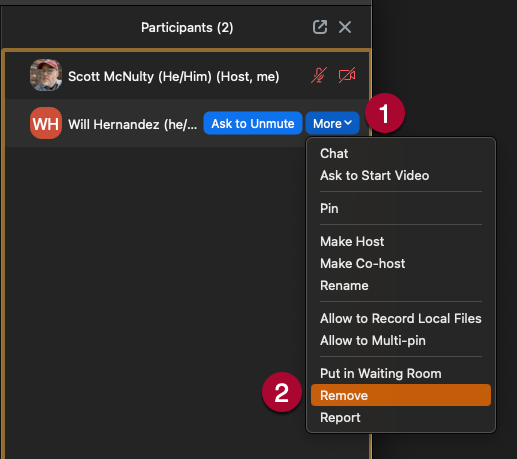
- Click on Remove to remove the selected participant.
- A confirmation popup appears. We recommend unchecking "Report to Zoom."
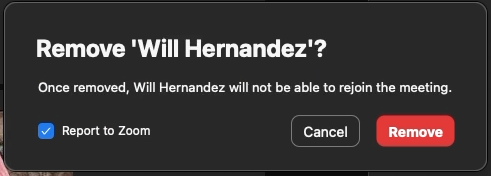
- Click Remove, and the participant is removed from your meeting and will not be able to rejoin.
- Repeat for each participant you'd like to remove.
Lock Meeting
You may want to stop additional people from joining your meeting for some reason. To do this, you need to "Lock" your meeting:
- Click the Shield icon labeled Host Tools at the bottom of your Zoom meeting window.
- A list of all the in-meeting security controls available to you appears. Click Lock Meeting at the top of the list.
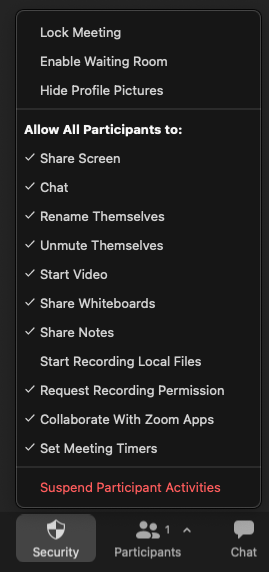
- An alert appears, letting you know that no one else can join the meeting.
Suspend All Activities
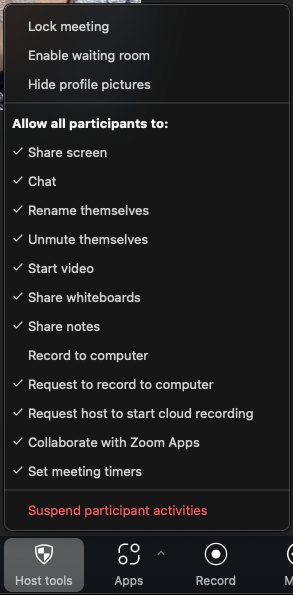
If there is a significant disruption in your meeting, you can suspend all participant activities with a few clicks. Be warned that this turns off most of the functionality of your Zoom meeting. Suspending all participant activities does all of the following:
- Mutes all video and audio.
- Hides all profile pictures
- Stops all active screenshares and turns off screensharing.
- Closes all breakout rooms.
- Stops the meeting recording if the meeting is being recorded.
- Turns off any Zoom apps active in the meeting.
- Locks the meeting, preventing anyone else from joining.
Once all activity has been suspended, you can use the "Remove Participant" directions above to remove the disruptive participant(s).
To Suspend All Participant Activity in a meeting:
- Click the Shield icon labeled Host Tools at the bottom of your Zoom meeting window.
- Click Suspend Participant Activity at the bottom of the list in red.
- Uncheck "Report to Zoom" in the notification, which also reminds you that you're about to turn off all the functions in your Zoom meeting.
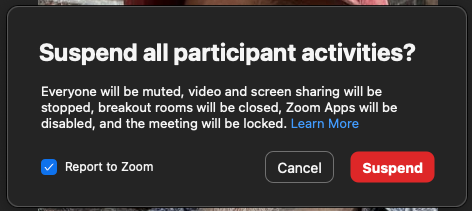
- Click the red Suspend button.
- You'll get a confirmation message that all activity has been suspended in the meeting.
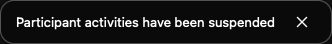
Once you've dealt with the disruption, you can turn on individual features by clicking the Host Tools icon and enabling each feature individually.
After Your Meeting
If any of your Zoom meetings are disrupted besides using the features above, report the incident to the Wharton Information Security Office (security@wharton.upenn.edu). They can engage additional resources, if needed, and offer any help you may require.
Questions?
Contact your Wharton Computing Representative or the Wharton Information Security Office for more information.