This article will give you an overview of what a firewall is, how it works, and will provide instructions on how to ensure your personal computer's firewall(s) are enabled.
Faculty & Staff: Faculty and Staff using Wharton-imaged or Wharton-provided devices may not be able to change Firewall (Crowdstrike) settings. This article applies only to personally managed computers.
For additional questions or requests, please reach out to your IT support representative or the Wharton Information Security Office at security@wharton.upenn.edu.
What is a firewall?
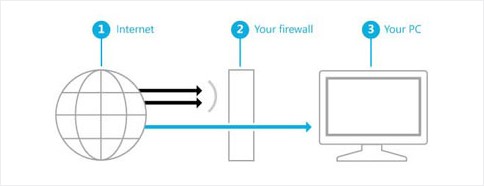
- A firewall is a network security system that establishes a barrier between a trusted, secure internal network and another network that may not be secure.
- Additionally, a firewall can help prevent hackers or malicious software from gaining access to your computer through a network or the Internet. A firewall can also help stop your computer from sending malicious software to other computers.
Enable/Disable Firewall
Warning: Only turn off your Firewall if you are installing a separate antivirus software that includes a firewall and active defender.
Windows
Follow Microsoft's directions on how to turn your Firewall on or off.
MacOS
Follow Apple's directions on how to turn your Firewall on or off.
Allow Trusted Applications
You can allow applications you trust. Only choose this option for applications you know are safe.
Questions?
Students - Wharton Computing Student Support
Faculty - Academic Distributed Representatives
Staff - Administrative Support
For more information regarding security threats and antivirus software, you can also contact the Wharton Information Security Office at security@wharton.upenn.edu.
